5 Step Data Security Plan for Small Businesses
by Trey Wilkins Main Articles PageIf you like the 5 Step Data Security Plan for Small Businesses article, please share it below.
Introduction
A recent Trend Micro survey that showed that only "49 percent of small companies view data leakage as a serious threat, while 63 percent were more concerned about viruses." Although it is understandable that more companies were concerned about viruses as opposed to data security leaks - for the simple reason that viruses are a more common occurrence - but data security leaks can be much more detrimental to the long term health of a small business.
Here is an alarming statistic that all small businesses should be aware of regarding data security leaks. On November 3, 2010, the Privacy Rights Clearinghouse released a report that among other items showed that "80 percent of small businesses that experience a data breach either go bankrupt or have severe financial difficulties within two years."
Small companies should be very concerned about data leakages, and let me share two examples of small business data security incidents I was involved with just in the past few months. In the first incident an employee left a company (let's call Company A), but the employee's email account was not turned off. There were no checks setup at Company A to delete employee access (email, network, etc), and the work email account was being forwarded to the former employee's personal email. While employed with Company A in a sales management role, the employee had setup a competing company, and when the employee left Company A, he continued to receive sales lead emails from Company A's clients. This continued for several months, and today Company A is having to spend several thousands of dollars in litigation in addition to facing the loss of several key clients.
The second incident involved a colleague of mine. Her healthcare provider's office was broken into, and the computer was stolen. This computer contained the financial and personal information of hundreds of patients. Personal banks accounts were accessed and money was stolen among other things. When a credit card is breached it is a major inconvenience, but it can be stopped relatively quickly. When a bank account is breached, it becomes a much more difficult issue to deal with and fix. This business lost the trust of hundreds of patients in addition to putting their financial and personal information at risk. This could have been easily prevented by encrypting the computer, which by the way can also be done for free.
I will reiterate the data leakage statistic..."80 percent of small businesses that experience a data breach either go bankrupt or have severe financial difficulties within two years." Small businesses should be very concerned about data leakage, and in this article, I will cover a 5 step security plan that every small business can follow to protect their assets. This 5 step security plan will be based off similar concepts that you will find in ISO 27001 data security, and although it will not be nearly as comprehensive as ISO 27001, it will be a strong foundation for protecting your company's assets.
Step 1 - Asset Identification/Classification and Risk Assessment
Identify Information Assets
The first step is to identify your information assets. Examples would be computers, phones, servers, fax machines, paper, flash drives/removable media, etc. A good rule of thumb is that if it contains client or business proprietary data, then it should be considered an information asset. Once you have identified your information assets, then you will need to tag and inventory the assets. It can be as simple as using the serial number and description of the asset and inventorying it in an excel spreadsheet to barcoding and tagging each asset and inventorying in a database. In addition assign an owner, generally a department head, for every asset.
Classify Information Assets
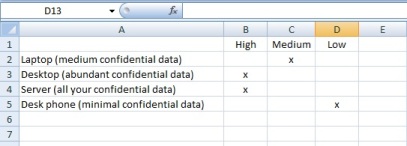
Once you have identified the assets, you need to classify them in a level of importance. Keep your classification system simple with High, Medium, and Low. Assets that contain client information or proprietary company information would obviously have the highest level of importance while assets that contain company marketing information might be given a low classification.
Risk Assessment of Information Assets
The final step would be to develop a risk assessment either for each asset class (eg. computers, phones, paper, etc) or for each asset classification (high, medium, low), and determine the risks you are willing to accept. You first need to determine the threat, vulnerability, and impact (TVI) on each individual asset or class of asset. The threat to the asset would list the different reasons/methods of how the asset could fail. The vulnerability is the situation that could lead to this failure. The impact is the influence of the effect on the integrity, confidentiality, and reasonable availability of the information asset.
Keep this process simple. Let's take a laptop for example. Although there are a multitude of threats, you should narrow down the list to the most common such as theft, virus, damage in transit, etc. The vulnerability for a laptop will obviously be higher because it may often be carried away from the office as opposed to a desktop computer. The impact of the loss of the laptop would depend on the data contained on the laptop, and you may choose to limit the data contained on a laptop because it is considered a more vulnerable asset.
Once you have determined the TVI for each asset or asset classification, you can then create a risk assessment matrix which is simply the impact a disruption to each asset or asset class would cause to your company, and the probability of it happening. Once again keep it simple, and just use High, Medium, and Low classifications.
The final step of the risk assessment process is to determine the level of risk you are willing to accept, and apply controls to manage the risks. Once again you should create risk classifications such as Tolerable, Moderate, Substantial, and Intolerable. When it is decided to apply controls to treat risks, the controls chosen should take into account the following:
- Any relevant state and national legislation that applies to your business area
- Your company's business objectives
- Operational requirements and constraints
- Cost of implementation and operation in relation to the risk being treated
- Investment costs of the controls in relation to the possible harm from a security failure
So let's now look at an example of identifying an asset, classifying it, determining the level of risk you are willing to accept, and the controls you put in place to protect the asset.
Asset: Network server that contains your company data
Classification: High because it contains classified and irreplaceable date.
Threats: HDD failure, virus, theft
Vulnerability: Medium - High
Impact: Very High
Level of Risk You Accept: You would want to take enhanced security measures such as keeping it locked up, behind a network firewall, and backed up. But it may be too expensive to backup your main server with a second server for real-time redundancy. In this case, to reduce costs but still ensure a backup in case of an emergency, you might be willing to accept a little added risk by backing your server up to tape which will require a longer downtime (takes longer to restore a backup tape) if the server was damaged.
Follow these steps, and you will clearly understand your information assets and the controls you need to put in place to protect them. And as you add new assets, update your database accordingly.
Step 2 - Network and Physical Access Security Controls
Network, Computer, and Email Access Controls
- Require all employees to use password authentication to access their computers, the corporate network, and email.
- Set computer passwords to expire every 90 days.
- Use strong passwords - Minimum of 10 characters, combination of at least 3 of the following 4 (letters, numbers, special characters, capitalized or lower-cased characters), do not use common words.
- It may be necessary to give employees different levels of access depending on the data stored on your corporate network. For example if you store personal client information (credit card, bank account, social security number, etc) on your corporate network, then you should determine which employees need access.
- Clear desk clear screen policy - All employees should be required to adhere to a clear desk, clear screen policy. When they leave their work computer, they should sign off to prevent an unauthorized user from accessing. You can setup a password protected screensaver that will activate after 10 minutes in case the employee forgets to sign out. In addition ensure that employees do not leave sensitive printed information on their desks unattended.
- Mobile computing - If you allow employees to access your corporate network via mobile access programs such as VPN, ensure that connections to your network are securely authenticated and that mobile computers are password protected. In addition consider passwords for employee mobile phones if the phones are used for company email access.
Physical Access Controls
- If you keep network servers on your company premises, then ensure they are encrypted and kept behind locked doors at a minimum. Limit employee access to servers.
- The type of corporate data you store on your company premises will have a direct impact on the type of physical access controls required. If the data is sensitive, then consider enhanced access security such as biometric, video cameras, third party security monitoring, etc. Many of these controls can be put in place rather inexpensively.
- If you host your corporate networks at a remote third party facility, keep it local if possible, and tour the remote facilities to ensure they have the proper physical and environmental protections.
Review of Access Controls
Once you have your physical and network security controls in place, it is crucial to review access controls. For example when employees leave your company, you want to ensure they no longer have access to any data. Your access control review schedule will depend on the amount of employee turnover at your company. If the turnover is more frequent, you should review access controls on a monthly basis. If it is less frequent, quarterly reviews will be more appropriate. You will want to check email, network, phone, mobile, and physical access controls. Set calendar reminders, and stick to the schedule.
Follow these steps to ensure proper network and physical security access controls in addition to setting a review schedule.
Step 3 - Network and Personal Computer Security Controls
Encryption
Encryption is probably one of the cheapest and most secure steps a small business can take. Encrypt your corporate server, work computers, laptops, flash drives, etc, and even if they are stolen, the data will still be safe from intrusion.
In addition if you send sensitive data via email, encrypt the emails using a program such as MessageLock
or PGP email encryption.
Anti-Virus/Anti-Spyware
Make sure you have anti-virus software on all of your work computers, and keep them updated. A good selection of anti-virus software.
Downloads and System Acceptance
Know the types of downloads you need to make to update and add software. In addition test new downloads and programs for system acceptance on an isolated (from your office network) system before running it company wide. Ideally run all downloads, upgrades, etc., through one person such as a network administrator or if you outsource to an IT company.
Firewall and Internet Connection
Ensure that you have your network or computers behind a firewall, and update it with security updates. In addition you should routinely (quarterly or bi-annually) scan your firewall for vulnerabilities and fix any issues. OpenVAS is a good free vulnerability scanning software.
Although I do not recommend it, if you use a wireless network in your office for your internet connection, use WPA2 encryption.
E-commerce
If you have an e-commerce site, use Secure Sockets Layer (SSL) for receiving or transmitting credit card information in addition to other financial data.
Network and Computer Backups
If you are a very small company with only a few computers, then you can easily backup to a flash drive or hard drive and take it offsite or keep it locked in a good secure (ie. bolted down) fireproof safe. In addition you should encrypt the flash drive, or any backup media for that matter. You also have the option of backing up to online sites like Mozy or Carbonite.
If you have a networked shop with multiple computers and servers, then backing up to tape is a good choice because it is inexpensive, and it is portable so you can send the tapes offsite to a storage facility. Setup a monthly or quarterly reminder to request one tape back at random from the offsite storage facility so you can conduct a test restore of the tape to check for corruption. In addition you will also get a feel for how accurate and reliable the offsite storage facility is in returning your tapes. Did they return the exact tape you requested? Did they return it when you requested? etc, etc.
No matter what type of backup you are doing, get in the habit of doing it on a regular schedule either daily, weekly, or a combo of both. If you have to do the backups manually, set up calendar reminders until it becomes a habit. Keep records of your backups. And do test restores from time-to-time to make sure there is no corruption of any kind.
Third party network security checks
In addition you should consider bringing in a third party at least once a year to check for additional network and computer vulnerabilities.
Follow these steps to ensure proper network and personal computer security controls.
Step 4 - Paper document controls
Information Classification Policy
The first step to securing your paper documents is to classify them. Keep your classification system simple, and I recommend no more than four classifications for document assets.
Examples
- Public - This type of information is not confidential and can be made public. Examples of this classification type are marketing materials.
- Proprietary - You would restrict this type of information to management-approved internal and external access. Examples of this classification type are policies and procedures. In some cases these document types may be required by clients to review the operational structure of your business.
- Client Confidential - Defined as information received from your customers that is proprietary and confidential. An example of this type of information is customer bank account info. This information type is restricted to management-approved internal access only.
- Company Confidential - This is confidential information that your company uses to conduct business. Examples of this type of classification are financial documents or personal employee information. You would tightly restrict access to this information within your company only.
Once you have classified your documents, consider setting up document templates and incorporate the document classifications which enable you to correctly monitor the dissemination of your documents.
Shred Documents
If any sensitive documents are marked as trash, then shred them. Keep documents that need to be shredded locked up until you shred them. This would also be part of your clean desk policy as you would not leave sensitive documents unmonitored on employee desks.
Filing Cabinets
Keep filing cabinets locked at all times, and if feasible keep them behind locked doors. Keep keys locked in a single location with limited access.
Follow these steps to ensure proper paper document security controls.
Step 5 - General security controls
Employee Background Checks and Training for new Hires
Run criminal history and credit background checks on your employees especially for those that will be handling sensitive information. Check their references both personal and professional. Review the Privacy Rights Clearinghouse Small Business Owner Background Check Guide to learn more about employee background checks.
In addition conduct training for new hires to make them familiar with your security policies and procedures.
Third Party Review
Depending on the sensitivity of the data stored at your office location, consider a third party review at least yearly. You could conduct a review of your complete security procedures in addition to network and physical security access.
Visitor Policy
If you have a constant flow of visitors to your office, consider a visitor policy. There are several options for a visitor policy, once again depending on the sensitivity the data stored in your office. Options include sign-in/sign-out sheet, ID check, name tags, and designated areas that are off limits to visitors without a company escort.
Incident Management System
Keep a system for logging any type of security incidents, how you corrected the issue, and how you will prevent it in the future. This can be as simple as an excel spreadsheet up to a tracking database.
Emergency Response Plan
Depending on the size of your company and the sensitivity of the customer data you store, the emergency response plan would be a key cornerstone of a business continuity plan (BCP). Smaller companies can almost use their emergency response plan as a BCP. Keep the emergency response plan simple and direct, and key elements to be included are as follows:
- A plan to determine who is in charge and who is responsible for each action covered below.
- Key personnel contact information - Obviously for contact but also to set in motion pre-assigned duties and responsibilities.
- Key contact information for service providers such as third party network administrators, security monitoring, phone, internet, etc.
- Key contact information for your local police in addition to your legal representation
- Backup communications plan
This concludes my 5 Step Data Security Plan for Small Businesses. There are of course additional layers of security procedures and policies you can add or subtract, and that is a decision you must make as a business owner to determine the level of protection needed for your data and your customer's data. If you have any questions, please do not hesitate to contact me today.
Share This Article






